A Guide to Quantum Security Concepts
As quantum computing advances toward practical reality, the cybersecurity landscape is undergoing a fundamental transition for “quantum-proofing”. Yet confusion persists around the terminology that defines this transition. If you've found yourself puzzled by terms like PQC, QKD, or "quantum-safe", you're not alone.
Let’s clarify these critical concepts that will shape the future of digital security.
We’ll begin by exploring two simple yet fundamental ideas in the quantum landscape.
1. Basic Quantum Notions
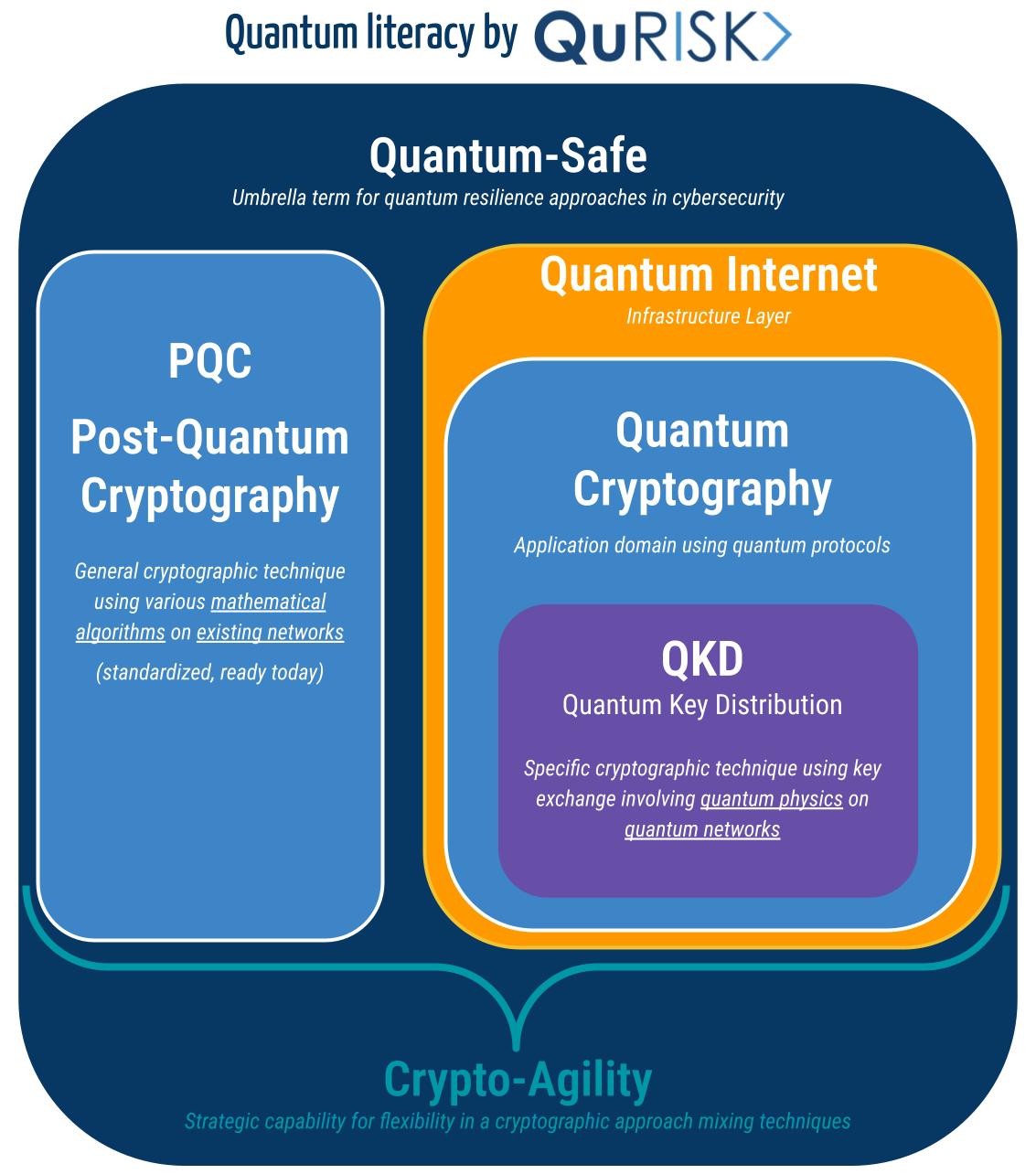
QUANTUM INTERNET
It is the infrastructure, analogous to how the classical internet provides the backbone for traditional computing and communication.
The quantum internet transmits qubits and includes components like quantum repeaters, optical fiber links, quantum memory, and classical control systems.
Here's what's crucial to understand: the quantum internet isn't meant to replace the classical internet. Rather, we're working toward a "quantum-enabled internet" that integrates both classical and quantum capabilities. While still experimental, this infrastructure will enable a new generation of secure communications.
QUANTUM CRYPTOGRAPHY
This represents a broad application domain using quantum mechanics principles for cryptographic purposes. It leverages a Quantum Communication Infrastructure (QCI) relying on quantum properties like superposition and entanglement to achieve secure communication.
With this setting in place, how do we build resilience?
2. Two Distinct Paths to Quantum Security
We explained in several of our publications the quantum threat and how quantum computers may break many of today’s classical cryptographic methods, which is why many organizations are now looking for cryptographic solutions that can resist attacks by a Cryptographically Relevant Quantum Computer (CRQC).
The confusion often starts here, because there are two different approaches to securing your data for the quantum era… and one of them doesn’t require any quantum infrastructure!
POST-QUANTUM CRYPTOGRAPHY (PQC): the mathematical Shield
PQC uses classical (non-quantum) algorithms based on advanced mathematical problems that remain difficult even for quantum computers to solve. These include lattice-based, hash-based, code-based, and multivariate cryptography approaches.
The beauty of PQC? It works on existing internet infrastructure, requires primarily software updates, and is ready for deployment today. NIST standardized several PQC algorithms in 2024, making this the most practical immediate solution for most organizations.
The downside? Well, PQC is “believed to be” quantum-safe, in other words we can only guarantee that there are currently no known methods to break PQC using CRQC.
QUANTUM KEY DISTRIBUTION (QKD): the physics-based Approach
QKD takes a completely different route, using quantum mechanics itself to securely distribute encryption keys. In QKD, eavesdropping is detectable due to the fundamental laws of quantum physics, offering what's called "information-theoretic security."
However, QKD requires specialized hardware and usually needs dedicated fiber optic connections, limiting practical deployment. It's important to note that QKD handles secure key exchange; you still need encryption algorithms to protect your data.
QKD is just ONE of MANY different quantum cryptography applications that we can perform by leveraging a quantum-enabled internet. Alongside, we have other applications such as Secure Delegated Quantum Computing (SDQC), quantum voting, and quantum money.
Now you may wonder: how to leverage these approaches to reach Quantum-Safety?
3. The Umbrella Term
QUANTUM-SAFE
Quantum-Safe (or quantum-resilient) cryptography actually encompasses both approaches, leveraging quantum cryptography (including QKD) and mathematical PQC to create a multi-layered defense, or complimentary layers defense against quantum threats.
In some quantum-safe architectures, QKD typically handles quantum key distribution through a quantum-enabled key management system, while PQC provides authentication. Together, they create robust protection against both current and future quantum threats.
A word of caution: there's no universal definition for "quantum-safe." Some use it to refer exclusively to PQC or QKD, so always clarify what's meant in context.
Ultimately, let's talk about agile resilience strategy.
4.The Strategic Capability
CRYPTO-AGILITY
Focusing solely on which technology to deploy misses a critical point. In an always-evolving threat landscape where new vulnerabilities emerge unpredictably, flexibility matters as much as the solution itself.
Which is why crypto-agility: the ability to quickly swap out cryptographic algorithms without major architectural changes, is one of the most important concepts to adopt.
We often hear this word in the context of PQC, but this isn't just about quantum threats. While crypto-agility certainly makes it easier to swap algorithms that are vulnerable to quantum attacks and allows a smoother migration to PQC, its value extends far beyond quantum-proofing.
Regulators worldwide are recognizing this imperative. ANSSI's position papers emphasize cryptographic agility as a fundamental security principle, while upcoming EU regulations like DORA, NIS2 and the Cyber Resilience Act increasingly mandate the capability to update cryptographic implementations. In the US, NIST's post-quantum cryptography migration guidelines explicitly require organizations to design systems with algorithm agility from the start.
Crypto-agility is your hedge against the unknown: future threats we can't yet anticipate, vulnerabilities yet to be discovered, and cryptographic breakthroughs that could emerge from unexpected directions. It provides architectural flexibility that transforms security from a fixed implementation into an adaptive capability, one that regulators now consider essential for resilient cybersecurity infrastructure.
CONCLUSION
QUANTUM LITERACY
Literacy is the ability to understand a specific area. And Quantum Literacy is what you just achieved by reading this article and making sense of the landscape!
Here’s a practical guide you can download (right-click on the image) with the main elements to keep in mind:
Your Practical Path Forward
For most organizations today, PQC represents the most practical path to quantum-safe security. It's standardized, deployable on existing infrastructure, and available now while quantum technologies continue maturing.
However, building crypto-agility into your systems ensures you can adapt as the technology landscape evolves. Whether quantum computers capable of breaking current encryption arrive in 5 or 10 years, the time to prepare is now.
The quantum revolution in cybersecurity isn't coming—it's already here. Understanding these fundamental concepts is your first step toward protecting your organization's digital assets in the quantum era.
By Mohamed Bassiouny, Quantum & Lab lead @ QuRISK - Quantum Risk Advisory.
✍🏻 Wanna discuss with the author of this article?
🛟 Need help on figuring out your quantum resilience journey?
🔐 Or you may just have early questions regarding your company's quantum safety ?
✅ … In any case, you can book a meeting on our website: www.qurisk.fr